Overview
Attribute-Based Access Control (ABAC) is an access-control model in which decisions are made based on attributes rather than static roles. Instead of assigning access through predefined roles, ABAC evaluates a set of user and resource attributes to determine whether access should be allowed at any given moment.
ABAC is also a core capability in Zero Trust Architecture (ZTA), enabling dynamic, context-aware access decisions based on continuously evaluated attributes.
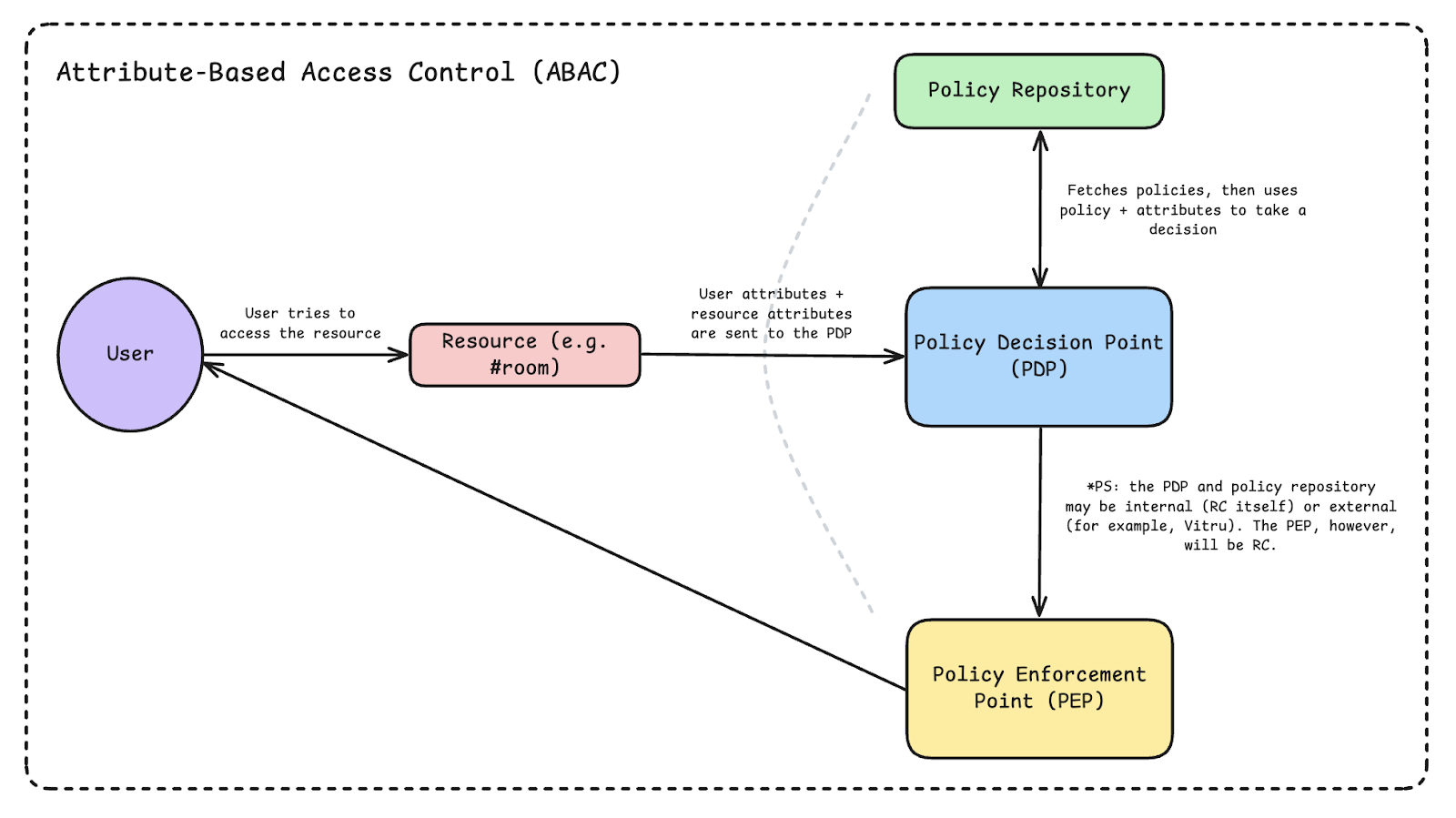
According to the NIST Guide to Attribute-Based Access Control, a typical ABAC system includes:
Policy repository: Stores the policies that define which attribute combinations grant or restrict access.
Policy Decision Point (PDP): Evaluates user and resource attributes against the defined policies and returns a decision (allow/deny).
Policy Enforcement Point (PEP): Applies the PDP’s decision by granting or blocking access in the application.
In practice, when a user attempts to access a resource, the PDP evaluates their attributes, compares them against the policy, and the PEP enforces the outcome, ensuring consistent, rule-based access.
ABAC in Rocket.Chat
Rocket.Chat introduces a native ABAC engine purpose-built for controlling access to private rooms, including private channels and private teams.
Key characteristics of Rocket.Chat’s ABAC system
Zero-Trust access model: Room membership is determined entirely by user attributes and is continuously validated. Administrators cannot manually bypass ABAC rules.
LDAP-driven attributes: All user attributes originate from LDAP. Rocket.Chat synchronizes only the attributes defined in the administrator’s mapping configuration.
Dedicated policy decision microservice:
Attribute evaluations are performed by a standalone, containerized PDP microservice.
The microservice is:
Horizontally scalable
Protected by strict timeouts and circuit breakers
Capable of emitting detailed decision logs
Forkable, allowing customers to extend or customize attribute resolvers without modifying Rocket.Chat core
Universal ABAC rule: A user may join or remain in an ABAC-managed room only if they possess all required attributes configured for that room.
Rocket.Chat’s ABAC enforcement process
Rocket.Chat automatically enforces ABAC decisions as part of room membership management:
Manual add restrictions: Admins can manually add a user to an ABAC-managed room only if that user already meets all attribute requirements.
Automatic removal: When a user’s LDAP attributes change or when room attribute requirements are updated, Rocket.Chat reevaluates membership after a sync is triggered via the ABAC Sync API (see Force a sync on revocations). Users who no longer qualify are removed within seconds.
Real-time attribute enforcement: Changes from LDAP are synchronized frequently, and admins can trigger immediate refreshes using the ABAC Sync API (see Force a sync on revocations).
Auditable actions: All ABAC-related events, including attribute updates, membership changes, and room configuration edits, are logged for compliance and traceability.
Architecture & Dataflow
Rocket.Chat’s ABAC implementation follows a modular, Zero-Trust-aligned architecture designed to evaluate and enforce room access decisions in near real time. The components work together to ensure membership is always accurate and auditable.
Dataflow overview
The following diagram illustrates the simplified dataflow behind ABAC evaluation and enforcement:
Policy Decision Point (PDP) Architecture
The Policy Decision Point (PDP) is a standalone microservice that evaluates whether a user’s attributes satisfy the requirements of an ABAC-managed room. It operates independently of the Rocket.Chat core application. The PDP evaluates user attributes against room requirements and returns a simple allow/deny decision. Key characteristics of the PDP microservice include:
Independent service: Runs separately from the main Rocket.Chat server.
Stable API interface: Communicates with Rocket.Chat using a stable API contract, aligned with the future plan to support external PDP integrations.
Containerized and horizontally scalable: Designed to scale with demand while maintaining low latency and high availability.
Robust reliability controls: Employs strict timeouts and circuit breakers to protect Rocket.Chat from slow or unresponsive PDP calls.
Detailed logging: Emits fine-grained decision and audit logs for compliance, debugging, and traceability.
Forkable for customization: Organizations may fork the PDP to implement custom attribute resolvers or integrations without modifying Rocket.Chat core.
Near Real-Time Enforcement
Rocket.Chat continuously monitors attribute changes and room configuration updates, re-evaluating access within seconds. Enforcement is triggered when:
User attributes change: Synced from LDAP through scheduled or forced attribute synchronization.
Room attribute requirements are modified: Admin-initiated updates immediately prompt membership reevaluation.
ABAC enablement is toggled: Activating or deactivating ABAC initiates a fresh round of checks to ensure compliance.
This near real-time model ensures that room membership always reflects current directory attributes and policy definitions, supporting strong Zero-Trust access control.
Together, these components form a predictable, auditable, and Zero-Trust-aligned access-control system for private rooms in Rocket.Chat.